
(Joey Harris/Unsplash)
About two weeks ago, just in time for Christmas, I got this email that struck me as bizarre, which didn’t seem like it made any damn sense.
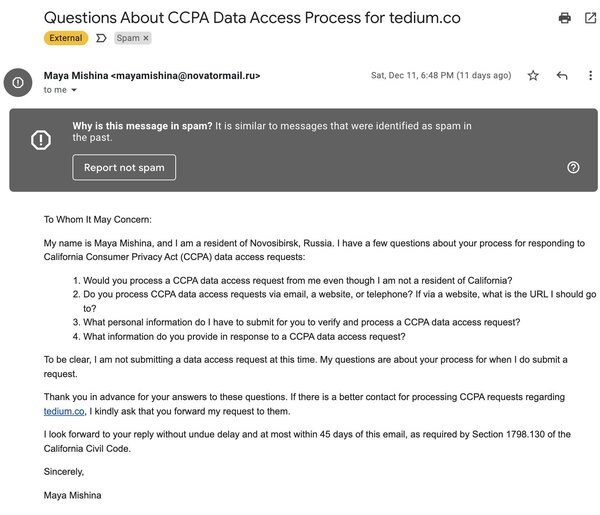
Basically, it was a user, based out of Russia, who was asking me for information about my process for handling data access requests under the California Consumer Privacy Act (CCPA). This struck me as strange, for a few reasons.
I know, from having written about CCPA in the past, that the law has specific legal carve-outs that basically exclude everyone except reasonably sized companies with tens of millions of dollars in revenue, or that are in the business of selling your data. Tedium, a project that basically is me-sized, doesn’t fit within the scope of CCPA.
Nonetheless, the email was worded as if a lawsuit was hitting my door in a few months.
“To be clear, I am not submitting a data access request at this time. My questions are about your process for when I do submit a request,” the email stated.
I did a search for the domain the email was sent from and I found few, if any search results, most from people like me wondering why they got this email.
Ultimately, I ignored the email, thinking it to be an exotic kind of spam, or a phishing attempt of sorts.
If you got this email, how would you react?
I was technically right about this, but the source of the phishing attempt, revealed a few days ago, is extremely unexpected.
The email was the creation of researchers at Princeton University, who were effectively trying to figure out how websites on the internet were complying with CCPA and its European equivalent, the General Data Protection Regulation.
As you might imagine, an email like this hit a few folks way larger than me, that work at companies that do fit under CCPA, that have lawyers on staff or on retainer that manage requests such as these, that feel like when they get a request like this, they have to take it seriously.
This type of email, for an academic researcher, is maybe a short amount of work. But for many businesses, what the email requests could be a significant burden, especially for those who haven’t done the work to properly comply with the law. It could cost them hundreds or thousands of dollars in billable hours from their legal team. And, as I previously said, the messages, which came from extremely exotic domains that only pulled up a few results on Google, could be interpreted as a phishing attempt, meaning they could lead to separate security compliance headaches for some companies.
https://twitter.com/jkosseff/status/1471816212732596227
Fortunately for all of us, cybersecurity law professor Jeff Kosseff of the U.S. Naval Academy was able to clear the air and point out that this was a very problematic approach.
“I respect everyone involved in the study and understand their goals,” he wrote in a Twitter thread. “I disagree with this approach to the research. I hope that they reach out to all recipients and inform them this was a study (if they haven’t already) so that the organizations can avoid more costs.”
Jonathan Mayer, the principal investigator of the study, posted an apology on the project’s website, and it’s clear that, from this perspective, the researchers didn’t think that part of the study through:
I have carefully read every single message sent to our research team, and I am dismayed that the emails in our study came across as security risks or legal threats. The intent of our study was to understand privacy practices, not to create a burden on website operators, email system operators, or privacy professionals. I sincerely apologize. I am the senior researcher, and the responsibility is mine.
As a result, they ended the study and apologized.
In a way, this reflects a problem with privacy regulations like CCPA and GDPR. Despite each regulatory structure in effect for a few years at this point, each is susceptible to being pressure-tested by random emails sent from anonymous people that, in cases such as these, could lead to costly and unexpected work just to understand if your organization needs to comply.
Put simply, this email, if your company got it today and it was actually real and not part of some misguided academic study, would be the opposite of a Christmas gift.
Time limit given ⏲: 30 minutes
Time left on clock ⏲: alarm goes off (twice in a row, need to work on that!)


